Check Point Research conducts Initial Security Analysis of ChatGPT4, Highlighting Potential Scenarios For Accelerated Cybercrime - Check Point Software

Countering Swarms: Strategic Considerations and Opportunities in Drone Warfare > National Defense University Press > News Article View

Detecting Biothreat Agents: From Current Diagnostics to Developing Sensor Technologies | ACS Sensors

The Chain Home Early Warning Radar System: A Case Study in Defense Innovation > National Defense University Press > News Article View
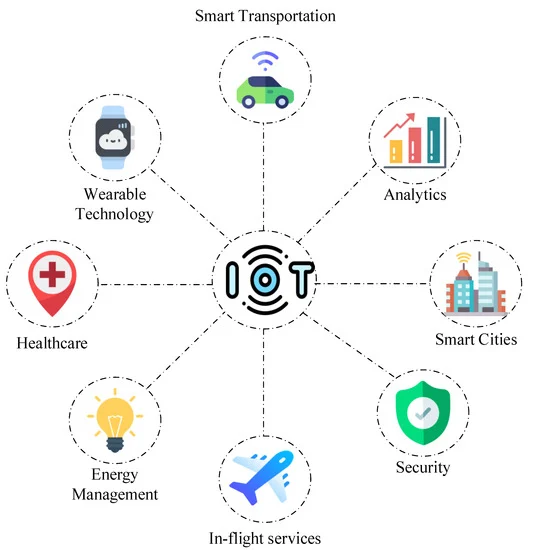
Sustainability | Free Full-Text | State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions

The Memory of the World in the digital age: digitization and preservation; an international conference on permanent access to digital documentary heritage

The Practical Psychic Self-Defense Handbook: A Survival Guide: Bruce, Robert: 9781571746399: Amazon.com: Books




![Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90] Inside Radio: An Attack And Defense Guide [PDF] [4223clofej90]](https://vdoc.pub/img/crop/300x300/7h70qulend40.jpg)






![Technology Trends in 2022 – Keeping Up [Full Book for Managers] Technology Trends in 2022 – Keeping Up [Full Book for Managers]](https://www.freecodecamp.org/news/content/images/2022/05/bohdan-orlov-Buwi_A04F6k-unsplash.jpg)
